Hi,
new features in Windows 10 prevents Virtual Machines based on VMware Workstation or Virtual Box from starting.
Typical Errors are:
- VirtualBox: VERR_SUPDRV_NO_RAW_MODE_HYPER_V_ROOT or VT-x is not available (VERR_VMX_NO_VMX)
error: Details: code E_FAIL (0x80004005), component ConsoleWrap, interface IConsole - VMware Workstation: VMware Workstation and Device/Credential Guard are not compatible. VMware Workstation can be run after disabling Device/Credential Guard
This features called Device Guard, Credentials Guard and Virtualization based security. They used the Microsoft Hyperviser Hyper-V to strictly separate parts of the Operating System.
According to: “There can only be one” no other hyper visor could started, because the VT-x or AMD-V CPU flags are not exposed to VMware Workstation or Virtual Box when Hyper-V is active.
You can check this by the systeminfo command.
D:\> systeminfo | findstr Hyper ... Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Be aware that the following steps disables some enhanced Windows 10 security features. Check this against your company policies to be compliant.
Disable Hyper-V launch, remove all Hyper-V features and set Registry Keys to disable virtualization based security
D:\> bcdedit /set hypervisorlaunchtype off D:\> dism /Online /Disable-Feature /FeatureName:Microsoft-Hyper-V-All /NoRestart D:\> reg add HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\LSA /v LsaCfgFlags /d 0 /f /t REG_DWORD D:\> reg add "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Device Guard" /v EnableVirtualizationBasedSecurity /d 0 /f /t REG_DWORD
Delete the Credential Guard and the VBS UEFI variables. To mount the UEFI partition determine an unused drive letter and set the environment Variable FREE_MOUNT_VOL_DRIVELETTER.
D:\> set FREE_MOUNT_VOL_DRIVELETTER=L:
D:\> mountvol %FREE_MOUNT_VOL_DRIVELETTER% /s
D:\> copy C:\WINDOWS\System32\SecConfig.efi L:\EFI\Microsoft\Boot\SecConfig.efi /Y
D:\> bcdedit /create {0cb3b571-2f2e-4343-a879-d86a476d7215} /d "DG" /application osloader
D:\> bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} path "\EFI\Microsoft\Boot\SecConfig.efi"
D:\> bcdedit /set {bootmgr} bootsequence {0cb3b571-2f2e-4343-a879-d86a476d7215}
D:\> bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} loadoptions DISABLE-LSA-ISO,DISABLE-VBS
D:\> bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} device partition=%FREE_MOUNT_VOL_DRIVELETTER%
D:\> mountvol %FREE_MOUNT_VOL_DRIVELETTER% /d
D:\> shutdown /t 0 /r
At next boot time this forces two prompts to disable Credentials Guard and virtualization based security. Accept both with F3.
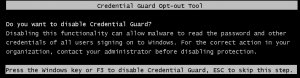
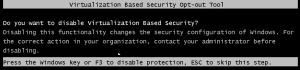
A tool is available to check if a driver is compatible with device guard code integrity. See also Driver Verifier
Michael
How can I re-enable them?
How can I re-enable them?
there is a typo in “HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Device Guard”
must be “HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\DeviceGuard”
Is there a way to not have to hit F3 upon reboot?
I access my machine remotely, which is sometimes rebooted without my knowledge.
Thanks,
Jeff
Hi,
can i use this article on my website ?
Hi Michael:
I have struggled with this issue, unable to run virtualbox on 64 bit machines, for the past full day. I tried many ideas until I realized that UEFI Boot and virtual security was blocking my effort. Then I narrowed my search to your article. I followed it along with the suggestion to correct one spelling error “DeviceGuard”. On first boot I got a BSOD with “WORKER_INVALID” message. But ignoring this message was all I needed to do.
Your article worked very well. Thank you.
AWESOME. Worked perfectly. I have struggled with this error for weeks, having to REINSTALL Windows 10 each time. What’s really irritating is that one of my machines is Windows 10 HOME, no Hyper-V (at least that’s what I thought), so I never considered Hyper-V related features to be the reason for this issue.
Thank you so much, I have been running with issues recently after Windows 10 auto-update. tried differnt solutions but this one worked!! You’re awesome mate!
Haven’t been able to use my VMs for over a month, finally found your page. I only was able to follow as far as up to the ‘mountvol’ stuff because there’s no ‘/s’ parameter in my version, but that was enough: I’m up and running now. Thanks!
Thank you for this, I kept getting errors saying invalid due to hypervisor and such and this fixed it. Thanks so much.
Holy MFJ (I am not Christian, I can say that..) you saved me from suicide.. Our Company has this in GPO, fortunately I have rights to overwrite it with our on Location, so I have disabled it in GPO, but problem persited. Thing is, it was already in place, so I had to delete the data from the section VBS UEFI variables. Now works!! VmWare/VBox, both works great 🙂 thank you a lot 🙂
Every time I restart my machine, I get the same thing. I get to start my VMWare Workstation once but when I reboot, I need to run the script again to reboot and F3 the solution. Would it be possible to persist the changes?
Hi Mike
I do get everything as mentioned in the post but i do not get second option so as to press F3 rather the moment I press F3 for the first time, after that it takes me to BIOS
Please let me know what wrong is here?
Thank you! I struggled with getting this all turned off.
Thanks so much! It was a huge pain in the ass before, but it was an even bigger one after the Windows 10 updates. Thanks so much for that last script, that was the critical component I was missing.
Great article.
Anyone figure out how to disable this without hitting F3?
THANK YOU! The official Microsoft instructions don’t explain how to disable Virtualization-Based Security at the same time as disabling Device Guard. Without disabling both of those at once, VMware Player is stuck depending on the inferior Microsoft Hyper-V API to run virtual machines. Now I can get back to running my VMs properly, without lag caused by Hyper-V.
I have this output:
mountvol %FREE_MOUNT_VOL_DRIVELETTER% /s
The parameter is incorrect.