Hi,
for deeper inspection of Windows it is sometimes necessary to get a memory dump of the machine to analyse these output with tools like volatility .
There are several ways to provoke windows to write a dump.
First of all set the option that Windows writes a complete memory dump. Do it with GUI
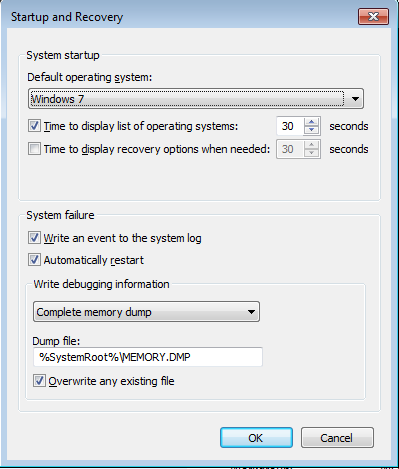
or set the option directly in the registry
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\CrashControl]
"CrashDumpEnabled"=dword:000000011. CrashOnCtrlScroll
Set the following registry keys
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\i8042prt\Parameters]
"CrashOnCtrlScroll"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\kbdhid\Parameters]
"CrashOnCtrlScroll"=dword:00000001
After rebooting your box, log on press and hold the right CTRL key down and press two times ScrollLock. Windows should crash with a BSOD, Stop Code 0xE2.
Note: This only works at the physical console not in a RDP Session because the key combination is recognized by the driver for physical keyboards. Keys stroke in a VMware ESXi Console session works.
2. NMI (Non maskable interrupt)
An NMI can be triggered either by physical hardware buttons or in virtualization environments by command line tools.
Prepare the Windows system by setting
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\CrashControl]
"NMICrashDump"=dword:00000001Reboot Windows and test it. If Windows is guest within a VirtualBox VM:
Identify your VM
c:\> VBoxManage.exe list vms
"Windows VM" {1ee41509-843f-4dea-bdb7-2dc2bd001ea4}
and trigger the nmi
c:\> VBoxManage.exe debugvm "Windows VM" injectnmi
Or as guest on a VMWare ESXi Server
Login to the ESXi Console or with ssh and determine the world id of the vm
~ # esxcli vm process list| grep -A 1 Win
Windows VM
World ID: 23445477
--
and send the nmi trigger
~ # vmdumper 23445477 nmi
Sending NMI to guest...
I have written a small Powershell script which sets and unset the registry keys for CrashOnCtrlScroll and NMI. It also enables the Windows Crashdump and set write debug information to “complete memory dump”.
Enable Crashdump, CrashOnCTRLScroll and NMI with
PS c:\> CrashControl.ps1 -e
Disable it with
PS c:\> CrashControl.ps1 -d
3. NotMyFault
Microsoft respectively sysinternals offers the command line tool NotMyFault to initiate a crash dump.
Usage is very simple 🙂
c:\> notmyfault.exe /crash
If you want to enforce a specific bugcheck code set the parameter /bugcheck 0xe2. Replace 0xe2 with your stop code.
c:\> notmyfault.exe /bugcheck 0x7b
NotMyFault has also so an interactive mode. To enter interactive mode start NotMyFault without any command line option.
Michael
