Hi,
when it is necessary that normal user needs the ability to do some operations on a service, such as starting or stopping, multiple ways exists to grant these permissions. Windows has no GUI or (easy to use) command line tool on board to set these access rights. I will show you 3 ways to set them.
- Sysinternals Process Explorer
- sc.exe (Service controller)
- subinacl.exe (The security swiss knife)
For the following examples I will use the OpenVPN Service with its Service Name openvpnservice and assign the start and stop permissions to a user or group. But its the same procedure for all other services.
The easiest way is to use the sysinternals Process Explorer. It provides a graphical user interface but has the dependency that the service must be in the running state before process explorer is started. If you already have a valid openvpn configuration start the service:
sc start openvpnservice
Then start the process explorer as administrator and locate the openvpn service process openvpnserv.exe.
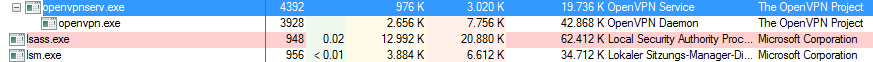
Right click, choose properties from the menu and select the service tab.
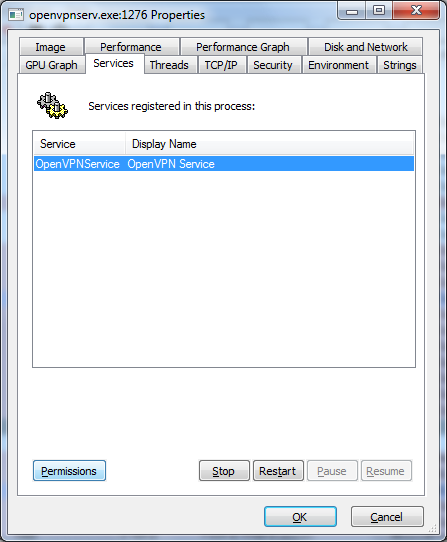
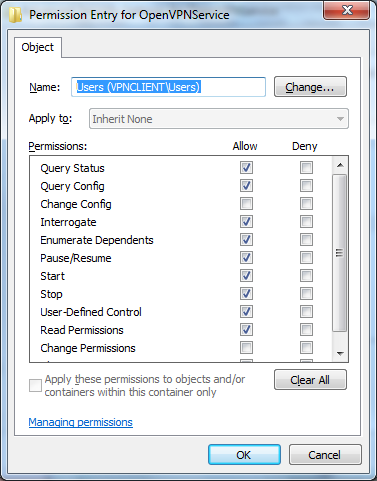
Press the permissions button and open the advanced settings. You can grant the various permissions to every User or Group. For example the start/stop/restart rights for the BuiltIn Users Group.
The permissions can also granted at command line with sc.exe (Service Controller) or the subinacl.exe (Command line ACL editor) . sc.exe is on board since Windows Vista , subinacl is part of the resource kit for Windows Server 2003 and is only available in a 32Bit version but already works for Windows Vista/7/8/8.1.
With sc.exe you have to edit or set the acls in sddl format. The sdshow option prints out the current persmissions. Editing the sddl is difficult but possible. See MSDN.
C:\>sc sdshow openvpnservice
D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCR
RC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
There is an easy way to get an valid sddl string :-). Open a management console mmc.exe and add the snapin “Security Templates”.
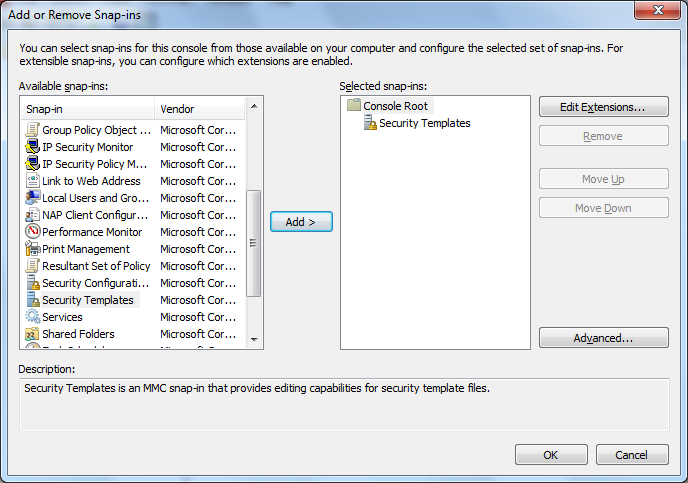
Create a new Template
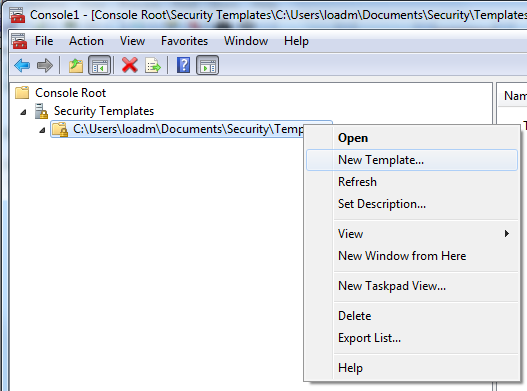
Locate the service
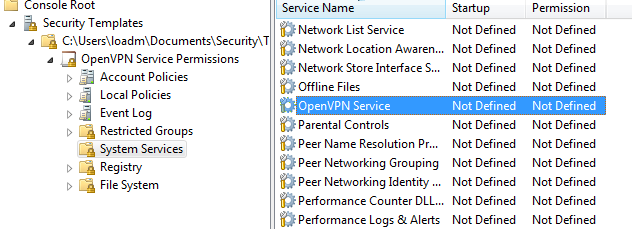
Name it “OpenVPN Service Permissions”
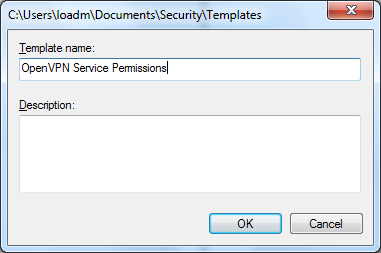
Define Startup Mode
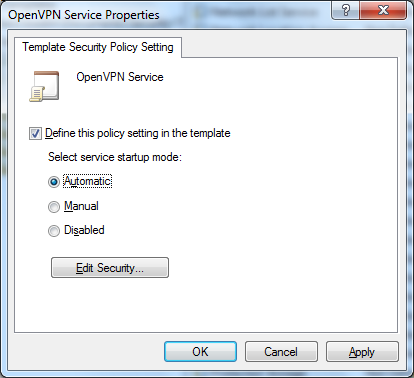
and permissions
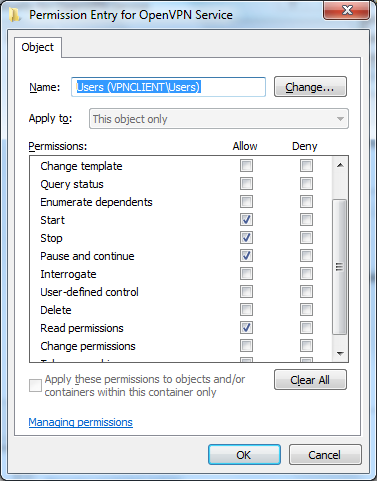
save the template and open the inf file, in my case the file C:\Users\loadm\Documents\Security\Templates\OpenVPN Service Permissions.inf. This should contains something like that:
[Unicode]
Unicode=yes
[Version]
signature="$CHICAGO$"
Revision=1
[Service General Setting]
"OpenVPNService",2,"D:AR(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;RPWPDTRC;;;BU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)"
Note: The template editor does not set the permissions itself, it only builts a inf file which can be imported by secedit. But we only need the sddl string:-)
This sddl string can be set by the sc.exe command:
sc.exe sdset openvpnservice D:AR(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;RPWPDTRC;;;BU)S:AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
[SC] SetServiceObjectSecurity SUCCESS
The 3rd way is to use subinacl.exe. This tool must be downloaded at microsoft. When downloaded, install the msi package.
msiexec /i subinacl.msi
You only have to install it one times. Than copy the subinacl.exe file to the hosts on which you want to use it.
The advantage against sc.exe is that you can modify an existing set of permissions.First of all ensure you have the correct version of subinacl.exe. The original version from the resource kit has many bugs. Check the version. This is the correct one.
D:\tmp>subinacl /?
SubInAcl version 5.2.3790.1180
This shows the currently defined permissions on the openvpnservice
D:\tmp>subinacl /service openvpnservice
========================
+Service openvpnservice
========================
/control=0x0
/owner =system
/primary group =system
/audit ace count =1
/aace =everyone SYSTEM_AUDIT_ACE_TYPE-0x2
FAILED_ACCESS_ACE_FLAG-0x80 FAILED_ACCESS_ACE_FLAG-0x0x80
SERVICE_ALL_ACCESS
/perm. ace count =4
/pace =system ACCESS_ALLOWED_ACE_TYPE-0x0
SERVICE_ALL_ACCESS
/pace =builtin\administrators ACCESS_ALLOWED_ACE_TYPE-0x0
SERVICE_ALL_ACCESS
/pace =interactive ACCESS_ALLOWED_ACE_TYPE-0x0
SERVICE_QUERY_CONFIG-0x1 SERVICE_QUERY_STATUS-0x4 SERVICE_ENUMERATE_DEPEND-0x8
SERVICE_INTERROGATE-0x80 READ_CONTROL-0x20000 SERVICE_USER_DEFINED_CONTROL-0x0100
/pace =builtin\users ACCESS_ALLOWED_ACE_TYPE-0x0
SERVICE_START-0x10 SERVICE_STOP-0x20 SERVICE_PAUSE_CONTINUE-0x40
READ_CONTROL-0x20000
Elapsed Time: 00 00:00:00
Done: 1, Modified 0, Failed 0, Syntax errors 0
Last Done : openvpnservice
You can get the full help text of subinacl with
subinacl /help /full
This command line adds the builtin Users group and grants the Query Service Configuration,Query Service Status,Start Service, Stop Service, Pause, Continue Service rights:
subinacl /service openvpnservice /grant=Users=QSTOP
Possible rights are
F : Full Control
R : Generic Read
W : Generic Write
X : Generic eXecute
OR
L : Read controL
Q : Query Service Configuration
S : Query Service Status
E : Enumerate Dependent Services
C : Service Change Configuration
T : Start Service
O : Stop Service
P : Pause/Continue Service
I : Interrogate Service
U : Service User-Defined Control Commands
Michael
If you want to centrally manage Windows service permissions without having to modify SDDL permissions on every machine, give System Frontier a try: http://systemfrontier.com/windows-services
Thanks 🙂
Wow,
Amazing. I fighted for 2 years nearly with subinacl / sc / other tools to setup this, and I already used Process Explorer for other purposes. I didn’t know this functionnality, you made my day mate 😉
Thanks again
nice this is what i look, and works completely