Hi,
these are the steps to protect a single file in a directoy by a password.
Continue reading Apache: Protect just one file in a directory by password
Hi,
these are the steps to protect a single file in a directoy by a password.
Continue reading Apache: Protect just one file in a directory by password
Hi,
if a User is logged on and forget it’s password you can dump to lsa process and recover the password from a dump file.
Two tools are needed:
Lets start. Login as a User with administrator permissions and dump the lsass process
Continue reading Windows: Recover lost passwords from memory
Hello,
last week I had to deploy 25virtual Windows (XP) Clients an on VMware ESX Cluster. One of the requirements was that the clients must be member of a Windows Active Directory.
After setting up vCenter (copy sysprep) I installed a reference Windows XP vm, convert them to a template and defined a Customization Specification like this:
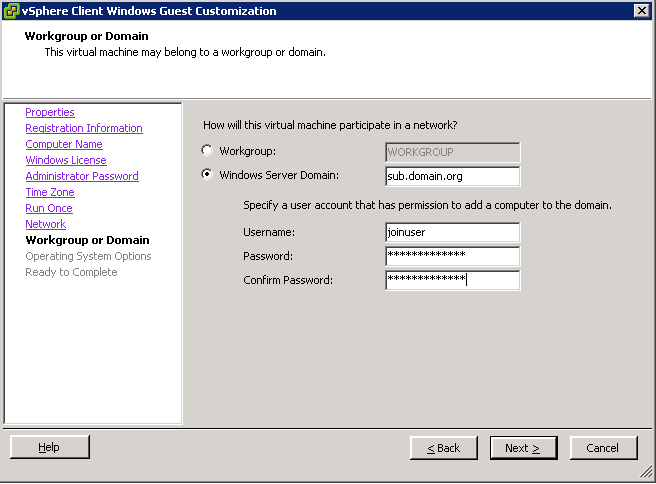
During the cloning process, by using the template with the recently created custom spec, the domain join always fails and the Computer Account was disabled at each try.
Ok, now I tried modify some parameter of the Custom Specification:
Continue reading VMware: Computer Account is disabled after deploying Windows Clients
Hi,
for test purposes it could be necessary to backup a computer by an image tool, i.e. Acronis TrueImage, and after the test is completed or in situations of a failure reset the computer back to it’s initial state by restoring the image.
In domain environments this could be a problem, because each computer which is member of a Windows Active Directory Domain is negotiating a password with the domain and this password is changed after 7 Days. If your Image is older the domain member ship is broken and you have to rejoin.
The password change is initiated by the client and this behaviour could be prevented by setting a registry value. Set this value, make an image afterwards and you will be able to restore the image as often you want or need without to leave the domain.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Netlogon\Parameters]
"DisablePasswordChange"=dword:00000001
Set it by command line
reg ADD HKLM\SYSTEM\CurrentControlSet\services\Netlogon\Parameters /v DisablePasswordChange /t REG_DWORD /d 1 /f
Have a nice day
Michael
=> Bug is solved in 5.1.0 Update 1a
Hi everybody,
since VMware vCenter 5.1 a new service SSO, the Single Sign On Service, handles the authentication for all logons. The advantage is that multiple authentication sources are possible. For example Local User and groups, OpenLDAP Directory Services and of course Microsofts Active Directory.
This post is related to vCenter Version 5.1.0b and describes how to add an Active Directory Domain as Identity source and get this running by using the “Reuse session” Authentication Type. The last one is the tricky part :-).
Let us start. Start the vSphere WebClient with a login which owns the appropriate rights, for example admin@system-domain or any other user who owsn has the SSO administrator privileges, and navigate to Administration/Sign On and Discovery/Configration. In the default configuration two identity sources are added by default. The SSO database and the user management of the local server.
To add an Active Directory as identity source the following informations are required
The attached powershell script GetSSOParameters.ps1 should determine this for your domain. You must start the script with the fully qualified domain name as parameter. Try it!
PS c:\>GetNetBiosDomainName.ps1 yourdomain.com
Basic Config for VMware SSO Identity source
NAME: YOURDOMAIN
Primary Server: ldap://domaincontroller1.yourdomain.com
Secondary Server: ldap://domaincontroller2.yourdomain.com
BaseDN Users: DC=yourdomain,DC=com
Domain: yourdomain.com
Domain Alias: YOURDOMAIN
BaseDN Groups: DC=yourdomain,DC=com
If you have the necessary information you can add the Identity source. See Screenshot below. First try to add by specifing a Username and a password which have the rights to query the Active Directory
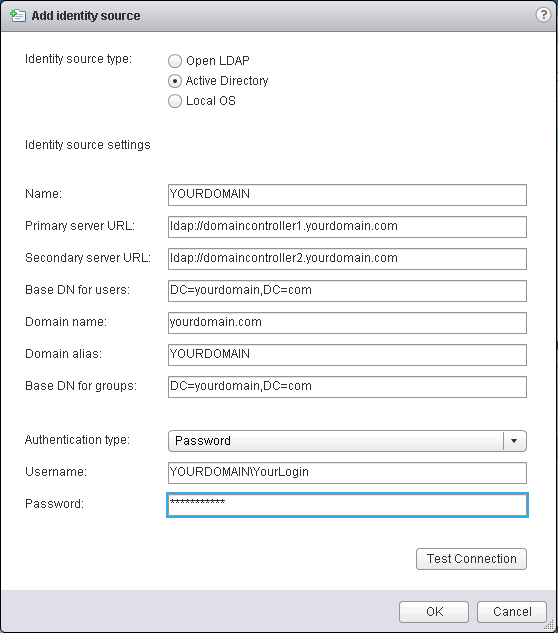
Press the Test Connection Button and normally this return that the connection is successfully established. Continue reading VMware vCenter: Howto add an Active Directory Domain as SSO Identity Source and using system session credentials